A policy is an object in AWS that, when associated with an identity or resource, defines their permissions. When you create a permissions policy to restrict access to a resource, you can choose an identity-based policy or a resource-based policy.
Identity-based policies are attached to an IAM user, group, or role. These policies let you specify what that identity can do (its permissions). For example, you can attach the policy to the IAM user named John, stating that he is allowed to perform the Amazon EC2 RunInstances action. The policy could further state that John is allowed to get items from an Amazon DynamoDB table named MyCompany.
Resource-based policies are attached to a resource. For example, you can attach resource-based policies to Amazon S3 buckets, Amazon SQS queues, VPC endpoints, AWS Key Management Service encryption keys, and Amazon DynamoDB tables and streams.
With resource-based policies, you can specify who has access to the resource and what actions they can perform on it.
To better understand these concepts, view the following figure. The administrator of the 123456789012 account attached identity-based policies to the JohnSmith, CarlosSalazar, and MaryMajor users. Some of the actions in these policies can be performed on specific resources. For example, the user JohnSmith can perform some actions on Resource X. This is a resource-level permission in an identity-based policy. The administrator also added resource-based policies to Resource X, Resource Y, and Resource Z. Resource-based policies allow you to specify who can access that resource. For example, the resource-based policy on Resource X allows the JohnSmith and MaryMajor users list and read access to the resource.
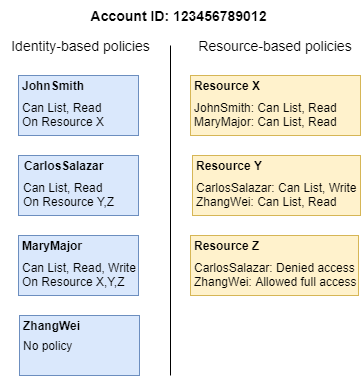
The 123456789012 account example allows the following users to perform the listed actions:
- JohnSmith – John can perform list and read actions on
Resource X. He is granted this permission by the identity-based policy on his user and the resource-based policy onResource X. - CarlosSalazar – Carlos can perform list, read, and write actions on
Resource Y, but is denied access toResource Z. The identity-based policy on Carlos allows him to perform list and read actions onResource Y. TheResource Yresource-based policy also allows him write permissions. However, although his identity-based policy allows him access toResource Z, theResource Zresource-based policy denies that access. An explicitDenyoverrides anAllowand his access toResource Zis denied. - MaryMajor – Mary can perform list, read, and write operations on
Resource X,Resource Y, andResource Z. Her identity-based policy allows her more actions on more resources than the resource-based policies, but none of them deny access. - ZhangWei – Zhang has full access to
Resource Z. Zhang has no identity-based policies, but theResource Zresource-based policy allows him full access to the resource. Zhang can also perform list and read actions onResource Y.
Identity-based policies and resource-based policies are both permissions policies and are evaluated together. For a request to which only permissions policies apply, AWS first checks all policies for a Deny. If one exists, then the request is denied. Then AWS checks for each Allow. If at least one policy statement allows the action in the request, the request is allowed. It doesn’t matter whether the Allow is in the identity-based policy or the resource-based policy.
