Gateway Endpoint are the endpoints that helps us to access the Amazon S3 services and Dynamo DB services. We can access these services using gateway Endpoint as well as through Public service endpoint like Internet Gateway.
Gateway VPC endpoints provide reliable connectivity to Amazon S3 and Dynamo DB services without requiring an internet gateway or a NAT device for your VPC. Gateway endpoints do not use AWS PrivateLink, unlike other types of VPC endpoints.
Overview
You can access Amazon S3 and DynamoDB through their public service endpoints or through gateway endpoints. This overview compares these methods.
Access the Services through Public Endpoint
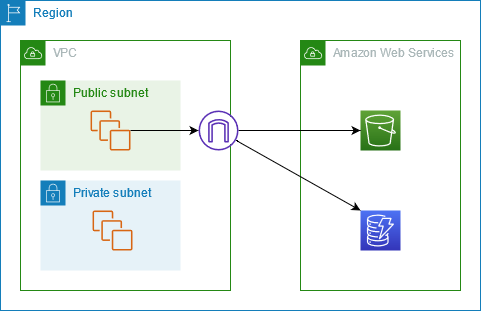
The following diagram shows how instances access Amazon S3 and DynamoDB through their public service endpoints. Traffic to Amazon S3 or DynamoDB from an instance in a public subnet is routed to the internet gateway for the VPC and then to the service. Instances in a private subnet can’t send traffic to Amazon S3 or DynamoDB, because by definition private subnets do not have routes to an internet gateway. To enable instances in the private subnet to send traffic to Amazon S3 or DynamoDB, you would add a NAT device to the public subnet and route traffic in the private subnet to the NAT device. While traffic to Amazon S3 or DynamoDB traverses the internet gateway, it does not leave the AWS network.
Access services through Gateway Endpoint
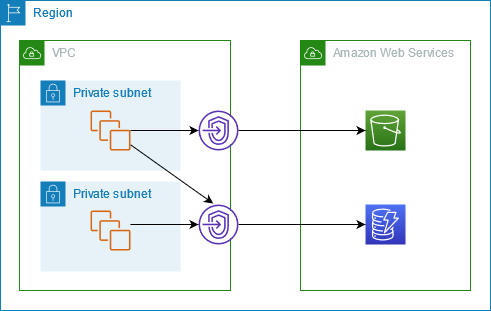
The following diagram shows how instances access Amazon S3 and DynamoDB through a gateway endpoint. Traffic from your VPC to Amazon S3 or DynamoDB is routed to the gateway endpoint. Each subnet route table must have a route that sends traffic destined for the service to the gateway endpoint using the prefix list for the service.
Routing
When you create a gateway endpoint, you select the VPC route tables for the subnets that you enable. The following route is automatically added to each route table that you select. The destination is a prefix list for the service owned by AWS and the target is the gateway endpoint.
| Destination | Target |
prefix_list_id | gateway_endpoint_id |
Security
When your instances access Amazon S3 or DynamoDB through a gateway endpoint, they access the service using its public endpoint. The security groups for these instances must allow traffic to and from the service. The following is an example outbound rule.
| Destination | Protocol | Port Range |
prefix_list_id | TCP | 443 |
The network ACLs for the subnets for these instances must also allow traffic to and from the service. The following is an example outbound rule. You can’t reference prefix lists in network ACL rules, but you can get the IP address ranges for the service from its prefix list.
| Destination | Protocol | Port Range |
service_cidr_block_1 | TCP | 443 |
